Vulnerability discovered: CDU files a complaint against a hacker

Vulnerability discovered
An IT expert discovered a security gap in a CDU election campaign app and reported it to those responsible. A little later, Lilith Wittmann announced on Twitter that the party had filed a complaint against the expert. As a result, the Chaos Computer Club directly announced in a public message that the CDU will no longer be reported to any more security gaps with immediate effect.The CCC also invokes what is known as Responsible Disclosure. This agreement actually protects IT people from legal consequences if they make companies aware of weaknesses. Because the CDU has now terminated this agreement with its notification, the CCC will refrain from reporting in the future. A few hours after the reports were posted on the Internet, the party withdrew the complaint and apologized. However, the process will not be discontinued, which is why Lilith Wittmann has already received financial support from followers. She had to pay a total of 2,000 euros for the criminal defense. The public prosecutor's office in Berlin could still stop the investigation. So far, however, there has been no statement from those responsible.
Read also 0
YouTube: Lawsuit against data transfer in Germany
YouTube is suing the Federal Government's Network Enforcement Act, which in future provides for an obligation to report to the Federal Criminal Police Office. 0EU Commission: Plans for digital tax off the table
Plans for a digital tax in Europe were terminated prematurely. Instead, the G20 countries want to introduce a global minimum tax. 0Cryptocurrencies: pressure from the federal government increases, providers should collect data
According to a current draft of the federal government, cryptocurrency providers may soon have to save and transmit personal data. var lstExcludedArticleTicker = '1377228,1376840,1375783,1374352'; Recommended editorial content Here you will find external content from [PLATTFORM]. To protect your personal data, external integrations are only displayed if you confirm this by clicking on "Load all external content": Load all external content I consent to external content being displayed to me. This means that personal data is transmitted to third-party platforms. Read more about our privacy policy . External content More on this in our data protection declaration. In addition to the CDU, Wittmann also informed the CERT Association and Berlin's data protection officer about the security gaps. The expert discovered the problems in the "CDU connect app" back in May. Datasets from over 18,000 election campaigners could be found unprotected on the Internet. In the meantime the apps for iOS and Android have been removed and the respective databases with the information taken offline.via Golem & Heise
INFRA:HALT Vulnerabilities Affect NicheStack: Industrial Devices Compromised
Researchers have discovered 14 bugs and stated them in a report, known as INFRA:HALT vulnerabilities. Their target is none other than a popular proprietary TCP/IP stack. More exactly the NicheStack variants that rank below 4.3 are subjects to threat. Who uses this kind of library? The industrial sector, counting over 200 vendors.
How Can an Attack Due to INFRA:HALT Vulnerabilities Work?All vulnerabilities were CVE classified. The ones who discovered them are the researchers from Forescout Labs and JFrog, the Forescout researchers having a project named Project Memoria that handles these issues.
According to Bleeping Computer, one of them, by his name Stanislav Dashevskyi, made a demonstration by taking one of the INFRA:HALT vulnerabilities and demonstrating how can it be exploited.
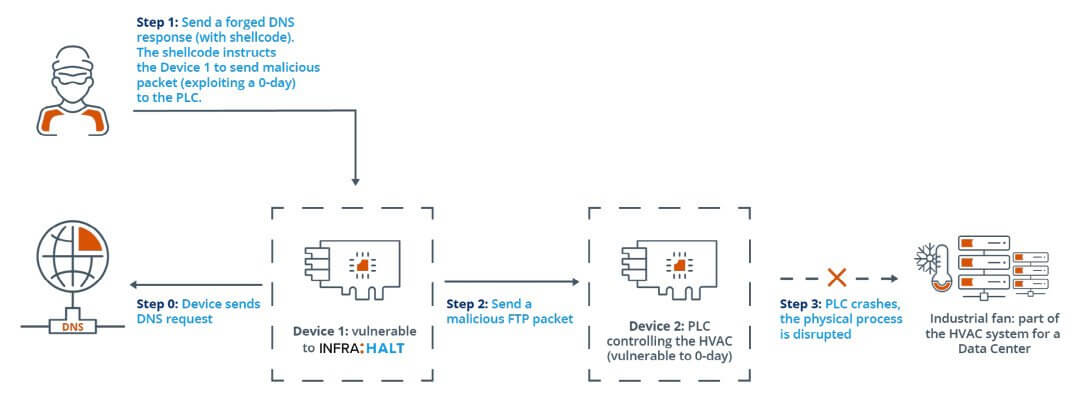

Image Source
The 14 Vulnerabilities: What They Do and How Dangerous They AreThe new vulnerabilities allow for remote code execution, denial of service, information leak, TCP spoofing, or DNS cache poisoning.
Source
The vulnerabilities pose a real threat to impacted devices. Most of them are high-security risks, but only 2 of them are critical. CVE-2020-25928 has a CVS score of 9.8 and CVE-2020-31226 has a score of 9.1.
However, they can be exploited only if hackers manage to get access to the internal network of the organizations. Granting access to the office network is not enough, but managing to connect to the OT section makes way for their malicious actions. Why? Because all the industrial equipment is deployed on that network.
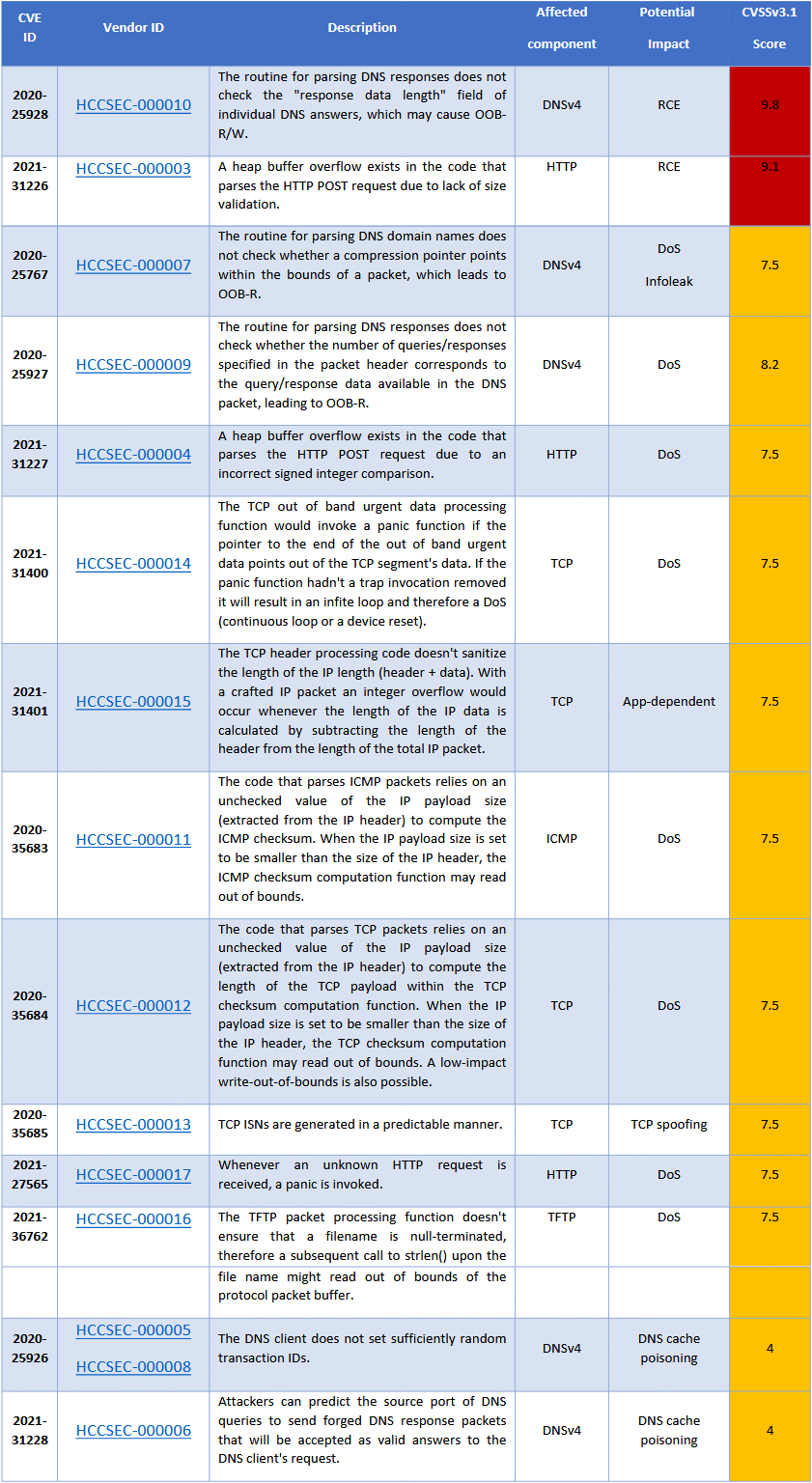

Image Source
How Many and What Devices Are Exposed?The number of affected industrial devices that use NicheStack raise to 6400.
Among targeted companies, these can be mentioned, that are NicheStack’s clients, known as InterNiches now because it’s under HCC Embedded at the present moment: Schneider Electric, Rockwell Automation, Honeywell, Emerson, Mitsubishi Electric, and Siemens.
According to the Forescout report, 21 vendors’ systems (2500) are impacted by these vulnerabilities.
What Measures Have Been Taken?HCC Embedded has taken the necessary measures and provided the proper patches that customers are urged to immediately apply. In short, all devices should be updated with the NicheStack 4.3 version.
Researchers from JFrog and Forescout also shared their mitigation recommendations where the above-mentioned patches cannot function:
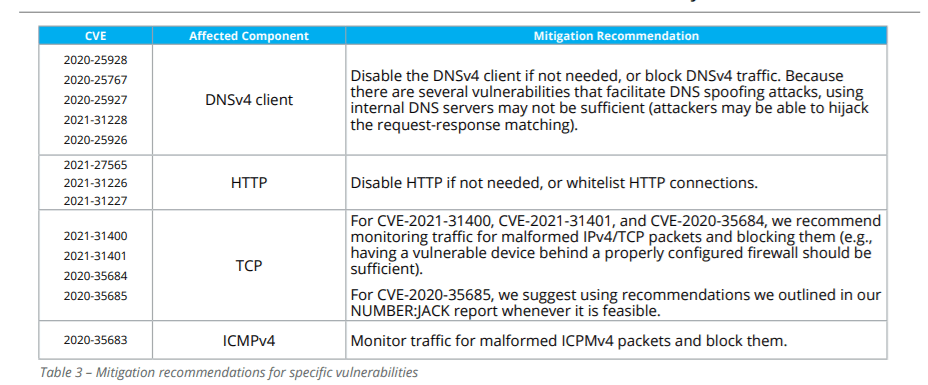

Image source
Also, according to the same report, researchers recommend to device vendors, network operators, and the cybersecurity community in general to: