These apps stole data and money from users, removed from the Google Play Store

These apps stole data and money from users
A group of eight applications was removed from the Google Play Store after a chilling discovery: these apparently harmless applications read users' SMS and subscribed to unwanted subscriptions. Here is the list of infected apps.McAfee security researchers Sang Ryol Ryu and Chanung Pak have discovered a group of eight applications on the Google Play Store that are really dangerous. The apps, now removed but which add up to over 700,000 downloads, were able to read users' notifications and SMS as well as activate unwanted subscriptions to be paid by the unfortunate.
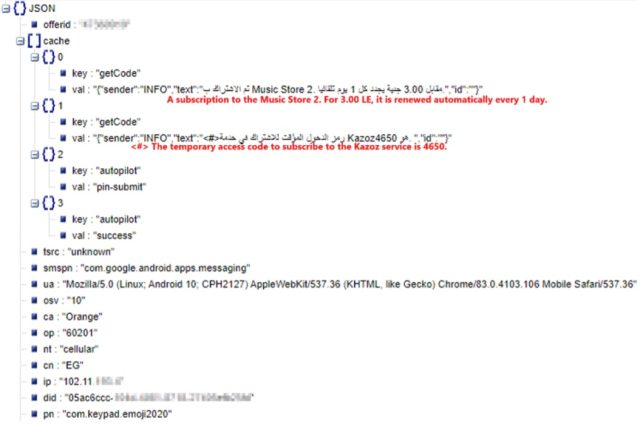
The couple of experts said that a investigation of the server that controlled the infected devices managed by the creators of the malware showed that all kinds of data were stored from users' phones. The collected data includes the telephone operator, telephone number, SMS messages, IP address, country and network status. The server also stored some auto-renewing subscriptions, some of which looked like the ones shown in the following image:
Credit: MacAfee Although this is a very similar type of attack to another malware discovered by recently named Joker, Etinu is part of a very distinct lineage. Despite this, security software from Microsoft, Sophos and other companies use the word Joker when they point to one of the newly removed apps in their scan results. This is perhaps because Etinu's decryption flow and the use of multistage payloads are similar to those of the "competition".
Credit: MacAfee “Malware hijacks Notification Listener to steal incoming SMS messages like Android Joker malware does, without SMS read permission,” the researchers wrote referring to Etinu. "Like a chain system, the malware then passes the notification object to the final stage. When the notification has emerged from the default SMS package, the message is finally sent [to the server] using the JavaScript WebView interface ".
The list of applications infected with this dangerous malware that can not only spy on you but also to rob activating unwanted subscriptions is as follows (each app is followed by their hash for more accurate recognition):
com.studio.keypaper2021 - 08C4F705D5A7C9DC7C05EDEE3FCAD12F345A6EE6832D54B758E57394292BA651 com.pip.editor.camera - CC2DEFEF5A14F9B4B9F27CC9F5BBB0D2FC8A729A2F4EBA20010E81A362D5560C org.my.favorites .up.keypaper - 007587C4A84D18592BF4EF7AD828D5AAA7D50CADBBF8B0892590DB48CCA7487E com.super.color.hairdryer - 08FA33BC138FE4835C15E45D1C1D5A81094E156EEF28D02EA8910D5F8E44D4B8 com.ce1ab3.app.photo.editor - 9E688A36F02DD1B1A9AE4A5C94C1335B14D1B0B1C8901EC8C986B4390E95E760 com.hit.camera.pip - 018B705E8577F065AC6F0EDE5A8A1622820B6AEAC77D0284852CEAECF8D8460C com.daynight.keyboard.wallpaper - 0E2ACCFA4 7B782B062CC324704C1F999796F5045D9753423CF7238FE4CABBFA8 com.super.star.ringtones for free. Poco X3 Pro is also available in Frost Blue color, you can find it on Amazon with 6GB of RAM and 128GB of internal memory.
Google Play apps with 700k installs steal texts and charge you money

Getty Images
Security researchers have uncovered a batch of Google Play apps that stole users’ text messages and made unauthorized purchases on users’ dime.
The malware, which was hidden in eight apps that had more than 700,000 downloads, hijacked SMS message notifications and then made unauthorized purchases, McAfee mobile researchers Sang Ryol Ryu and Chanung Pak said Monday. McAfee is calling the malware Android/Etinu.User data free for the takingThe researchers said an investigation of the attacker-operated server that controlled infected devices showed it stored all kinds of date from users' phones, including their mobile carrier, phone number, SMS messages, IP address, country, and network status. The server also stored auto-renewing subscriptions, some of which looked like this:
 No jokeThe malware is reminiscent, if not identical, to a prolific family of Android malware known as Joker, which also steals SMS messages and signs up users for pricey services.
No jokeThe malware is reminiscent, if not identical, to a prolific family of Android malware known as Joker, which also steals SMS messages and signs up users for pricey services.“The malware hijacks the Notification Listener to steal incoming SMS messages like Android Joker malware does, without the SMS read permission,” the researchers wrote referring to Etinu. “Like a chain system, the malware then passes the notification object to the final stage. When the notification has arisen from the default SMS package, the message is finally sent out using WebView JavaScript Interface.”
While the researchers say that Etinu is a malware family distinct from Joker, security software from Microsoft, Sophos, and other companies use the word Joker in their detection names of some of the newly discovered malicious apps. Etinu’s decryption flow and use of multi-stage payloads are also similar.
Advertisement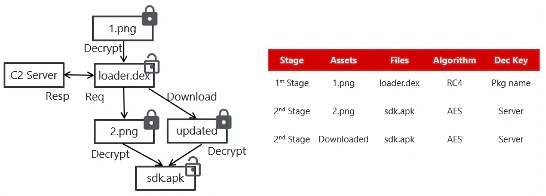
The decryption flow.
McAfee
In an email, McAfee’s Sang Ryol Ryu wrote: “While Etinu looks very similar to Joker, in-depth, its processes for loading payloads, encryption, targeting geographies are different from Joker.”
The Etinu payloads appear in an Android Assets folder with file names such as “cache.bin,” “settings.bin,” “data.droid,” or 'image files.'
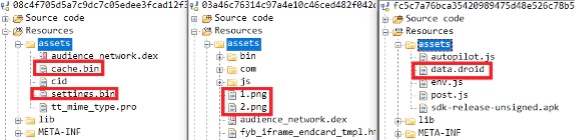
McAfee
Multi stageAs depicted in the decryption flow diagram above, hidden malicious code in the main installation file downloaded from Play opens an encrypted file named “1.png” and decrypts it using a key that’s the same as the package name. The resulting file, “loader.dex” is then executed, resulting in an HTTP POST request to the C2 server.
“Interestingly, this malware uses key management servers,” the McAfee researchers wrote. “It requests keys from the servers for the AES encrypted second payload, ‘2.png.’ And the server returns the key as the ‘s’ value of JSON. Also, this malware has self-update function. When the server responds ‘URL’ value, the content in the URL is used instead of ‘2.png’. However, servers do not always respond to the request or return the secret key.”
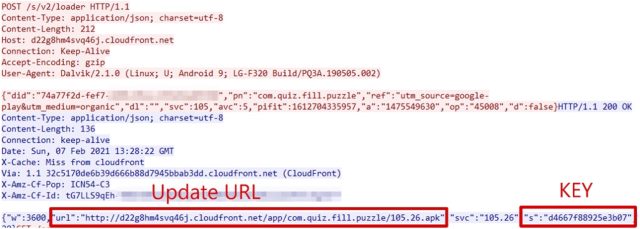
McAfee
The apps and corresponding cryptographic hashes are:
08C4F705D5A7C9DC7C05EDEE3FCAD12F345A6EE6832D54B758E57394292BA651com.studio.keypaper2021CC2DEFEF5A14F9B4B9F27CC9F5BBB0D2FC8A729A2F4EBA20010E81A362D5560Ccom.pip.editor.camera007587C4A84D18592BF4EF7AD828D5AAA7D50CADBBF8B0892590DB48CCA7487Eorg.my.favorites.up.keypaper08FA33BC138FE4835C15E45D1C1D5A81094E156EEF28D02EA8910D5F8E44D4B8com.super.color.hairdryer9E688A36F02DD1B1A9AE4A5C94C1335B14D1B0B1C8901EC8C986B4390E95E760com.ce1ab3.app.photo.editor018B705E8577F065AC6F0EDE5A8A1622820B6AEAC77D0284852CEAECF8D8460Ccom.hit.camera.pip0E2ACCFA47B782B062CC324704C1F999796F5045D9753423CF7238FE4CABBFA8com.daynight.keyboard.wallpaper50D498755486D3739BE5D2292A51C7C3D0ADA6D1A37C89B669A601A324794B06com.super.star.ringtonesSome of the apps look like this:
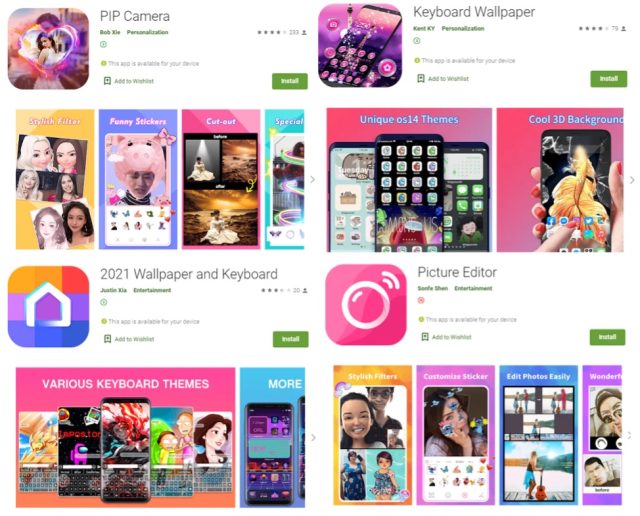
McAfee
The researchers said they reported the apps to Google, and the company removed them.